PHP & SQL Security
I was looking for answer to a security related question, and I found this Whitepaper for web security measures a programmer must know.
A Dozen Programming Tips
I was thinking about what to write when my friend suggested about this topic. It does not mean that I am a good programmer. It only means that after so many years I just know how to manage a program when needed.
- Start with an easy to learn programming language, like Pascal. This will help you to learn programming rather than the programming language. After you learn programming, you can easily go to complex programming languages like C, C++, Java, etc.
- Use your time to learn the art of programming. Peter Norvig once said that we need at least 10 years to learn programming. He was right to a certain extent as more we learn programming, more we come to know about our ignorance.
- Make programming a fun exercise as to maintain the interest for such a long time.
- Learn to be lazy. It is not at all necessary to write each and every program from scratch. Maintain a library of your own and use the programs when you can. But, you must have a good library.
- My mom says that a person can be a good cook only if he had eaten good food. Same applies here, so go through as many programs as you can. Analyse them using scientific methods and classify them properly before adding it to your library.
- Get so involved in programming, that when some program is not running, you think of it as how to solve it. My experience says that most problems are solved in dreams. Make sure you wake up as soon as you find the solution. 😀
- Talk to other programmers and take help from them. Similarly, help other programmers when you can. This may result in learning new things that you never knew.
- Join a gang or a community of programmers where you discuss programming and criticize each others work.
- Work on projects with other programmers. Be the best programmer on some projects; be the worst on some others. When you’re the best, you get to test your abilities to lead a project, and to inspire others with your vision. When you’re the worst, you learn what the masters do, and you learn what they don’t like to do (because they make you do it for them).
- When you meet a good program try to understand it inside out. Experiment with it as much as you can. What happens when you make a change? Ask as many questions as you can and try to find the answers.
- Analyzing problems correctly helps to solve the problem correctly. But, good analysis is learnt only by practice. So, when you go somewhere try to see if you can develop a solution using programming. Even if it is a small problem like your household budget, or your pocket money management.
- You should know at least a half a dozen programming languages. this makes you aware of different programming practices used in in different programming languages. But, keep in mind that all the programming languages support different programming features like class abstraction, functional abstraction, Syntactic abstraction, declarative specifications, coroutines, parallelisms, etc. Or it may be based on frameworks like, .NET, MVC, etc.
Well, I will finish here. But there are many other things that need to be considered while writing a good program. But, I guess programmers already know it. Happy Programming.
References:
Teach Yourself Programming in Ten Years – Peter Norvig <http://norvig.com/21-days.html>
Published: 2001, Last Accessed : August 25, 2008 at 11:39 a.m. IST
Tips for choosing the right Content Management System(CMS) for your Website
Thinking about adding a CMS to your website or thinking about implementing a CMS type solution to your website? Don’t know where to start, well have no fear, I am here to give you some tips on choosing the right CMS for your website A content management system, or CMS, is a web application designed to make it easy for non-technical users to add, edit and, well, manage content, articles, and blog posting. Using a CMS for your site means that you can easily update data on the site while maintaining the style look and feel( via skinning). I am going to specify which CMS you should use BASED on what you want to accomplish for your site:
Information security
Information security means protecting information and information systems from unauthorized access, use, disclosure, disruption, modification, or destruction.The terms information security, computer security and information assurance are frequently used interchangeably. These fields are interrelated and share the common goals of protecting the confidentiality, integrity and availability of information; however, there are some subtle differences between them. These differences lie primarily in the approach to the subject, the methodologies used, and the areas of concentration. Information security is concerned with the confidentiality, integrity and availability of data regardless of the form the data may take: electronic, print, or other forms.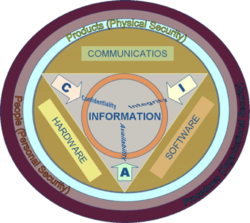



Governments, military, financial institutions, hospitals, and private businesses amass a great deal of confidential information about their employees, customers, products, research, and financial status. Most of this information is now collected, processed and stored on electronic computers and transmitted across networks to other computers. Should confidential information about a businesses customers or finances or new product line fall into the hands of a competitor, such a breach of security could lead to lost business, law suits or even bankruptcy of the business. Protecting confidential information is a business requirement, and in many cases also an ethical and legal requirement. For the individual, information security has a significant effect on Privacy, which is viewed very differently in different cultures.
The field of information security has grown and evolved significantly in recent years. As a career choice there are many ways of gaining entry into the field. It offers many areas for specialization including Information Systems Auditing, Business Continuity Planning and Digital Forensics Science, to name a few.
This article presents a general overview of information security and its core concepts.
Firewall
Definition
A firewall is a device or set of devices configured to permit, deny, encrypt, or proxy all computer traffic between different security domains based upon a set of rules or other criteria.
Function
A firewall is a dedicated appliance, or software running on another computer, which inspects network traffic passing through it, and denies or permits passage based on a set of rules.
A firewall’s basic task is to regulate some of the flow of traffic between computer networks of different trust levels. Typical examples are the Internet which is a zone with no trust and an internal network which is a zone of higher trust. A zone with an intermediate trust level, situated between the Internet and a trusted internal network, is often referred to as a “perimeter network” or Demilitarized zone (DMZ).
A firewall’s function within a network is similar to firewalls with fire doors in building construction. In the former case, it is used to prevent network intrusion to the private network. In the latter case, it is intended to contain and delay structural fire from spreading to adjacent structures.
Without proper configuration, a firewall can often become worthless. Standard security practices dictate a “default-deny” firewall ruleset, in which the only network connections which are allowed are the ones that have been explicitly allowed. Unfortunately, such a configuration requires detailed understanding of the network applications and endpoints required for the organization’s day-to-day operation. Many businesses lack such understanding, and therefore implement a “default-allow” ruleset, in which all traffic is allowed unless it has been specifically blocked. This configuration makes inadvertent network connections and system compromise much more likely.